How MCP gateway works
Writer’s MCP gateway sits between WRITER Agent and partner MCP servers. This architecture provides centralized security, access control, and observability for enterprise deployments. You can use the MCP gateway to connect your WRITER Agent to supported connectors. Connector requests flow through the following steps:- Client connection: WRITER Agent connects to Writer’s unified MCP server
- Request submission: WRITER Agent sends HTTP requests to the MCP gateway endpoint
- Authentication: The gateway validates user identity and permissions using your Writer organization’s access controls
- Request routing: Authenticated requests are routed to the appropriate partner MCP server
- Response delivery: Results are returned to the agent through the secure channel
Available connectors
Writer provides connectors to enterprise tools across multiple categories. Below is a list of currently supported connectors.| Connector | Auth type | Provider authentication docs |
|---|---|---|
| FactSet | OAuth 2.0 | View docs |
| Gmail | OAuth 2.0 | View docs |
| Gong | API key + Tenant URL | View docs |
| Google Calendar | OAuth 2.0 | View docs |
| Google Docs | OAuth 2.0 | View docs |
| Google Sheets | OAuth 2.0 | View docs |
| HubSpot | OAuth 2.0 | View docs |
| Microsoft Calendar | OAuth 2.0 | View docs |
| Microsoft OneDrive | OAuth 2.0 | View docs |
| Microsoft Outlook | OAuth 2.0 | View docs |
| Microsoft SharePoint | OAuth 2.0 | View docs |
| Microsoft Teams | OAuth 2.0 | View docs |
| PitchBook | API key | View docs |
| Slack | OAuth 2.0 | View docs |
Set up connectors
Connector setup happens in AI Studio under Connectors & Tools. For step-by-step instructions on configuring connectors, selecting tools, and managing permissions, see Setting up connectors. The sections below cover the technical authentication requirements for connectors.Set up connector authentication
The three types of authentication for connectors are OAuth 2.0, API key, and tenant-based. The type of authentication required for a connector depends on the third-party service, and the connector configuration flow in AI Studio guides you through the required setup. OAuth 2.0 connectors (FactSet, Google, Microsoft, Slack, HubSpot):- Most OAuth connectors support WRITER-managed authentication (no OAuth app setup required)
- Alternatively, you can create your own OAuth application for custom branding and control
- FactSet, Slack, and HubSpot require organization-managed OAuth (WRITER-managed not available)
- See Set up OAuth for details on both options
- Require an API key from the third-party service
- Some services require additional configuration like tenant URLs
- See the available connectors table for links to the provider’s documentation on how to create API keys
- Uses an API key and an additional tenant URL to authenticate requests
- Require your organization’s specific instance URL. For example:
https://yourcompany.gong.io - Used to identify your organization’s instance in multi-tenant services
Set up OAuth
Most OAuth connectors support two authentication options in AI Studio: WRITER-managed OAuth (recommended for most users):- Writer provides and manages the OAuth application
- No OAuth app setup required
- Users authorize access to their account when they first use the connector
- Faster setup with less configuration
- You create and manage your own OAuth application with the provider
- Provides more control and custom branding
- Requires OAuth app configuration with client ID and client secret
- Required for: FactSet, HubSpot, Slack
FactSet, HubSpot, and Slack connectors only support organization-managed OAuth. All other OAuth connectors support both options.
OAuth connection levels
When configuring an OAuth connector, you choose whether to use user-level or org-level authentication: User-level OAuth (most common):- Each user connects their own personal account (their Gmail, Slack, etc.)
- OAuth authentication happens when individual users first try to use the connector
- Administrators configure the connector in AI Studio, but don’t authenticate during setup
- Users authenticate through WRITER Agent the first time they interact with the connector
- A single shared OAuth connection for the entire organization
- OAuth authentication happens during connector setup in AI Studio
- Administrators authenticate with the provider when configuring the connector
- Users can immediately use the connector without individual authentication
With user-level OAuth, administrators set up the connector configuration (OAuth app credentials, enabled tools, access permissions), but the actual OAuth authentication happens later when each user first uses the connector. With org-level OAuth, administrators complete the OAuth authentication during the initial connector setup.
Create OAuth applications for organization-managed authentication
If you choose organization-managed OAuth, or if using a connector that requires it, you need to create an OAuth application with the provider:- Follow the provider’s documentation to create an OAuth application. View the available connectors for links to provider documentation.
- Add the following Writer redirect URI to the list of allowed redirect URIs in your OAuth application’s settings:
- Copy the client ID and client secret for use in AI Studio
Required OAuth scopes
Each connector requires specific OAuth scopes to access third-party APIs. The connector configuration interface in AI Studio displays the required scopes when you configure a connector.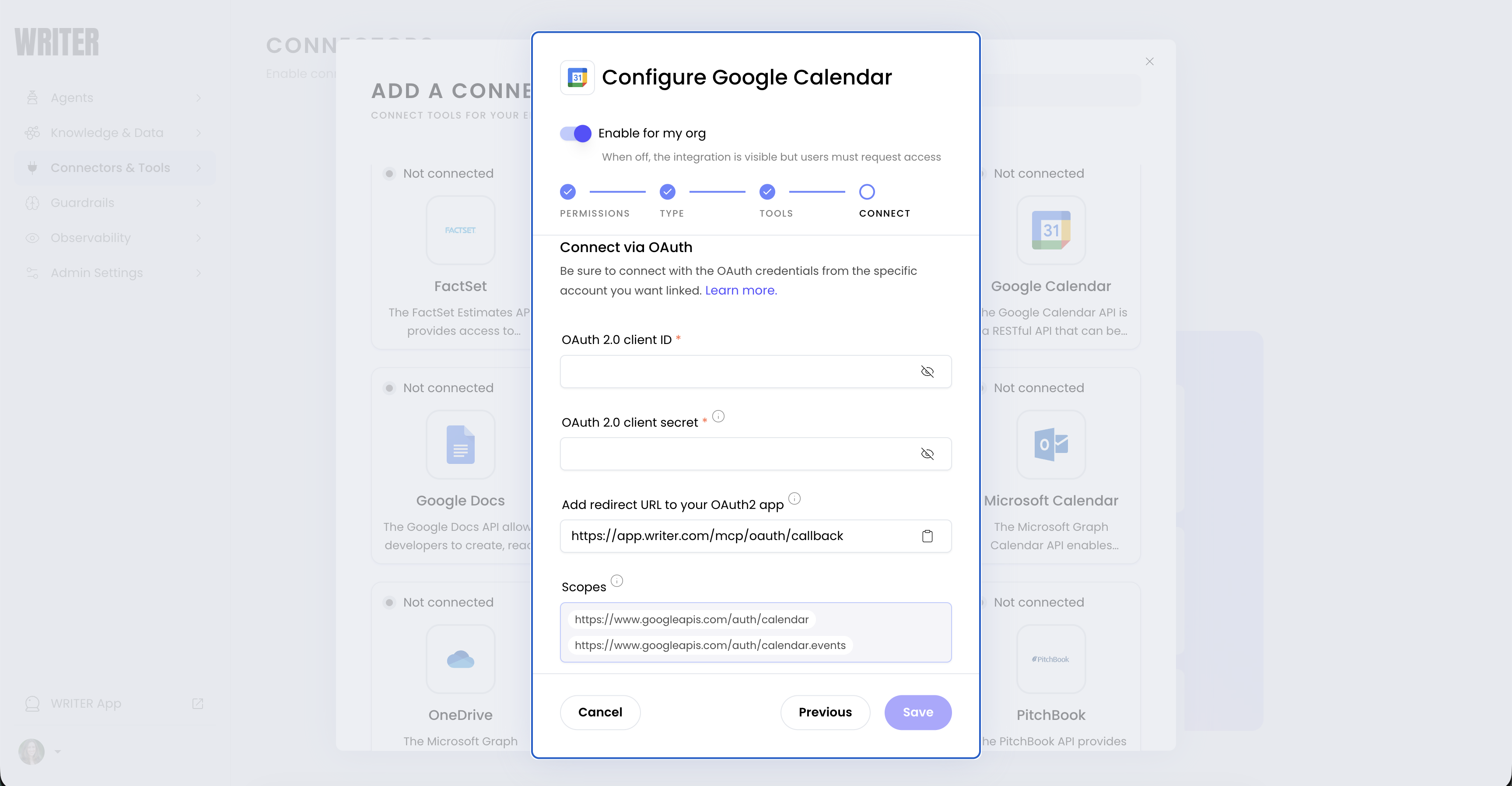
- Read and search documents
- Create and modify files
- Access calendar events
- Send messages or notifications
- Manage sharing permissions
Currently, OAuth scopes are fixed per connector and do not adjust based on which tools are enabled. This means users will see requests for all scopes even if you’ve disabled certain tools.
Manage access control and permissions
Organization and IT administrators can control which users have access to connectors and configure granular permissions for connector functionality.Configure connector availability
Connectors can be made available to users in two ways:- All users: The connector is immediately available to everyone in the organization
- Select teams: Restrict the connector to specific teams. Users on non-approved teams can request access, which requires admin approval.
Role-based administration
By default, only users with Org Admin and IT Admin roles can configure and manage connectors. These permissions can be adjusted through the roles and permissions settings in AI Studio to delegate connector management to other roles if needed.Tool-level granular control
Within each connector, administrators can selectively enable specific tools rather than activating all available functionality. This provides fine-grained control over what actions AI agents can perform through each connector. For example, you might enable read-only tools for a connector while disabling tools that modify or delete data.Revoke connector access
Administrators and users can revoke connector access at multiple levels: Revoke individual user access:- Users can disconnect their personal OAuth accounts from within WRITER Agent settings
- Disconnecting removes the user’s authentication tokens but preserves the connector configuration
- Users can reconnect by re-authorizing through the OAuth flow
- Administrators can disable a connector entirely from AI Studio’s Connectors & Tools interface
- Disabling a connector immediately revokes access for all users
- Re-enabling requires users to re-authenticate with their accounts
- Administrators can disable individual tools within a connector without removing the entire connector
- Users retain their OAuth connections but cannot access disabled tools
- Tool permissions can be re-enabled without requiring re-authentication
Connect as an end user
After administrators configure connectors in AI Studio, end users interact with them naturally through conversation in WRITER Agent.User-level vs. org-level OAuth
Connectors can be configured with different OAuth authentication levels, which affects how users connect: User-level OAuth (most common):- Each user connects their own personal account (their Gmail, their Slack workspace, etc.)
- Users authenticate individually with their own credentials
- The connector accesses only that user’s data and permissions
- Example: When you use the Gmail connector, it accesses your Gmail inbox, not a shared organizational inbox
- An administrator sets up a single OAuth connection for the entire organization
- All users share the same authenticated connection
- No individual user authentication required
- Less common; typically used when accessing shared organizational resources rather than personal accounts
Most connectors use user-level OAuth where each person connects their own account. When a connector is configured with user-level OAuth, users must authenticate individually before using it.
How users interact with connectors
To use a connector, just ask the WRITER Agent for what you need in everyday language, like “Summarize my emails” or “Find messages in Slack.” If access is needed, the agent will let you know and help you connect your account. After you’re connected, you can keep making requests the same way—no special steps or commands required. Example interactions: Using Gmail:First-time connection flow
For connectors configured with user-level OAuth, users must authenticate their personal account the first time they use a connector:- User makes a request: “Search Slack for messages about the budget”
- Authentication prompt: Agent responds: “I need access to your Slack workspace to search messages. Please connect your Slack account.”
- OAuth authorization: User clicks the authentication button and is redirected to Slack’s authorization page
- Permission consent: User reviews the permissions and approves access
- Return to conversation: User is redirected back to WRITER Agent
- Task completion: Agent automatically retries the original request: “I found 15 messages about the budget…”
Known limitations
OAuth token expiration
Some providers automatically expire OAuth tokens after periods of inactivity:- Google services: OAuth credentials become invalid after 6 months of inactivity. If you haven’t used a Google connector (Gmail, Google Calendar, Google Docs, Google Sheets) for 6 months, you’ll need to re-authenticate.
Fixed OAuth scopes
OAuth scopes are fixed per connector and do not adjust based on which tools are enabled. This means when you configure an OAuth connector, the OAuth application requests all scopes needed for every available tool, even if you disable certain tools in your connector configuration.Next steps
- Set up connectors: Learn how to configure and enable connectors in AI Studio.
- Tool calling guide: Understand how AI agents use tools in conversations.
- Action Agent guide: Learn how to use Action Agent with connected tools.
- API reference: Explore the Chat Completion API that powers tool calling.